|
What Social Engineers Prey onRead the content, attempt the challenges and where additional information is required watch the videos. Credit to:Circadence AuthorityThis is the idea that people follow the lead of credible, knowledgeable experts or do as commanded by people who are seen as authoritative figures, this is in hope of some sort of reward or in fear of getting into trouble. Social engineers look to take advantage of these acts of human nature, to create the image of authority some of the following techniques are used: - Titles: using managerial titles such as Manager, CEO, Director, etc. - Wealth: having materialistic items can give the impression that someone has money therefore somewhat an authority over others. - Clothing: wearing high vis clothing or a smart suit can make people appear more important than they actually are. Using any combination of some of the above examples can aid social engineers into tricking targets into believing they have some sort of authority which in turn improves the chance of a successful attack i.e. gaining access to a building or retrieving someone’s password. An example scenario that can convey authority is the following: Arriving at a target's office in a fancy car while wearing an expensive suit will assist expressing authority and can fool individuals into letting you access the building. On the other hand, if you are communicating with a target via email use of authoritative titles such as technical support or student help desk can trick individuals into sharing sensitive information. 
Which one of the following is not a technique used by social engineer’s to create the image of authority?
Choose 1 answer IntimidationThis principle may not be something that is directly aimed at you from the engineer, instead, the attacker might create a situation that can make you feel intimidated and influence you into doing something you don’t want to do. An example scenario would be a co-worker saying that if you do not tell them about some sensitive information then they will inform the boss about your poor customer service and treatment which could result in being disciplined or dismissed. This same situation could be applied to an educational enviroment, where the co-worker could be a classmate threatening to frame you for plagiarizing if you do not help them with an assessment or provide your login credentials. 
Which of the following is true in terms of the intimidation principle?
Choose 1 answer Social ValidationSocial Validation is one principle that can be easily exploited and this is because of the common way that people make decisions of what to believe or how to act in a situation, this is generally done by looking at what other people are believing or doing. Social validation may also be referred to as social proof or consensus. This is especially effective when the targets are uncertain, as they will often look to the actions and behaviours of others to determine their own. A good example of social validation in practice would be attackers persuading individuals to install Trojan malware software. The targets are more likely to install a Trojan if everyone seems to indicate it is safe. Another example of social validation implemented into a social engineering attack would be, for instance, a social engineer creating a professional-looking form that asks for the individual’s computer login details. The attacker could say that these are required for a yearly university/college security assessment. Upon giving the form to the target, the attacker may say “Numerous of your fellow students [dropping names of other members in the organization to help legitimize the request] have already completed this form, it is essential for you to do the same.” The target now presented with this false statement feels more at ease thanks to the assumption that others have followed suit. Social proof is especially effective when the target is not around his or her peers. Without being able to confirm the attacker’s false claims, lone victims can be more easily convinced to disclose information than those who are within a group. 
What is an effective technique used by social engineer’s looking to exploit the social validation principle?
Choose 1 answer ScarcityScarcity is an element that is used to exploit human nature in everyday life thanks to online and television advertisements. The seller will claim that there is a limited amount of stock available or that a special offer runs out soon, one example of scarcity in everyday life would be Apple iPhones. When Apple first release the new version of the iPhone, they almost always sell out within minutes. Apparent scarcity raises the demand for products, which is why social engineers often create a sense of urgency in order to manipulate the target. The scarcity rule states that “individuals assign more value to opportunities when they are less available". The scarcity principle is effective for two main reasons. Firstly, because things that are difficult to attain are usually more valuable and secondly, as things become less accessible, we lose freedoms”. Social engineers will use the same tactics that legitimate companies like Apple use to fool vulnerable individuals. One way this can be done is through phishing emails. Non-legitimate social engineers can exploit this and entice the target to click a link for access to a limited time offer on a product. Once the user clicks the link, they will be diverted to a malicious web site. The website that the targets are diverted to are often bogus websites that look extremely similar to legitimate websites such as Amazon or eBay. The unfortunate individual tempted by the offer and the limited time sale on the product buys the item, they then send the social engineer his or her name, address, and credit card information. In return, the buyer receives a false receipt. In the meantime, the attacker swiftly buys various items with the newly acquired credit card information. One thing students should watch out for is phishing emails regarding SAAS. Attackers may send emails pretending to be from SAAS saying that the spaces for your course are almost full and if you don't apply for funding soon you may miss out, or that there was a problem sending out money for your student loan and that you are required to provided banking details. Social engineers are also interested in stealing logins to SaaS sites because they yield financial data and also personnel data, which can be used to launch further attacks. If you are unsure about recent emails received by SAAS or would like to know more please visit https://www.saas.gov.uk/files/376/saas-fraud-policy.pdf. 
What is the scarcity rule?
Choose 1 answer UrgencyAttackers tend to introduce some sort of urgency to the social engineering attack, which can allow for the attack to move along quicker. Urging the targets that something needs to be carried out quickly can give the victims little time to think about what malicious intents might be behind the engineer’s requests. The engineer might say something along the lines of “Simply give this information immediately so that we can solve this issue” or “In order for this to be resolved you must carry out what I say at once”. Here is an example of urgency being employed in an attack. Attackers can use bogus security alerts like the following to trick vulnerable individuals who believe if they do not act upon the alert, they will lose their precious data: 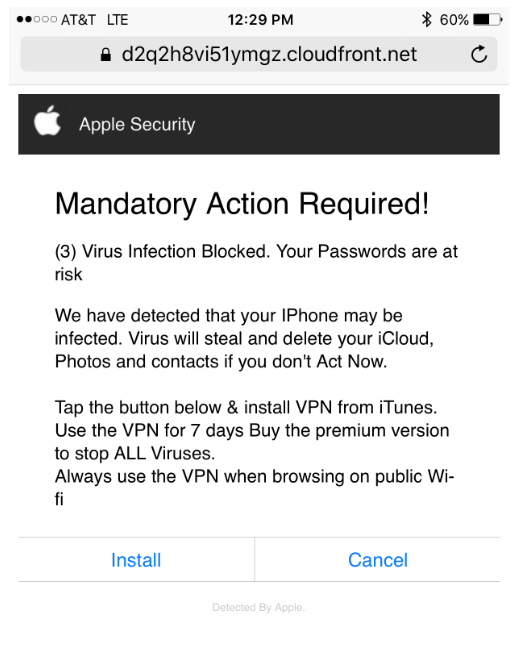
What can attackers use to trick vulnerable individuals into falling for their trap?
Choose 1 answer Familiarity/Liking/TrustOne other principle that is used in social engineering is one of familiarity, liking and trust. This is where the engineer makes an attempt to befriend the target. This can be done by speaking about things that the target enjoys, and by doing that, they make you comfortable with them which in return can make you more likely to carry out tasks for them. Needless to say, the social engineer is going to make an effort to create trust between you and them. They will try to convince you that they’ll be able to resolve all of your issues and all you have to do is trust them and provide the information they desire. This principle tends to be effective as its part of human nature to be more responsive to others whom they are friendly with and like. This rise in responsiveness helps attackers looking to exploit friendliness. Being more responsive means that the target is more prone to say “yes” to requests from friends or colleagues. As a result of befriending the target, an attacker taking advantage of social engineering will flatter and compliment the target during their interactions. A person is more inclined to reveal information to someone who is kind-hearted, thoughtful, and courteous. An example of these characteristics being exploited could be a receptionist who works at an organization, his or her job means they are essentially the gatekeeper to the other members within the organization. An attacker could walk in an explain to the receptionist that they are late for a meeting with an executive within the organization. They also explain how they cannot remember the office or phone number of the exec and asks the receptionist for the executive’s information while being polite and smiling. Whether the receptionist is male or female, the attacker will attempt to include a compliment to further the friendliness front in hopes of the receptionist giving out the desired information. 
Which of the following is not a technique an engineer can use to befriend a target?
Choose 1 answer ReciprocityReciprocity is a straightforward principle that takes advantage of the fact that people feel obliged to give back to others, whether that be in the form of behaviour, gift, or service that they have received originally. This principle works due to the human response of feeling a sense of debt to the provider of a good or service for getting something for nothing. In most cases of receiving goods or services, the debt is repaid in monitory amounts. Manipulating this feeling of guilt is easy and one of the highly common strategies used by social engineers. Exploiting this principle requires the social engineer to make the first move rather than waiting for the target to engage with the attacker. Some ways you can see the reciprocity principle taking place in everyday life is for example when a friend invites you to their party, there is an obligation for you to invite them to any future parties you may host or if a classmate does you a favour then you may feel you now owe that classmate a favour in return. Another example of this with evidence is shown when you are given the bill at a restaurant, there is often a small sweetie such as a mint or a lollipop included with the bill. Studies have shown that giving customers something as simple as a mint has helped increase tips by approximately 3%. Unbelievably if the token of goodwill is increased to say two mints the tip doesn’t just double it quadruples to an astonishing 14% tip. Furthermore, if the waiter presents one mint, begins to walk away from the table, but pauses, turns back, and says, “For you nice people, here’s an extra mint,” tips increase again and go to 23%. 
What does the reciprocity principle require the social engineer to do?
Choose 1 answer Feel you've learned enough? Click the image below to test your knowledge of Social Engineering Principles 
Return to top of the page If you have completed the above you may move onto the Types of Attacks page Click here to move on 1 |
